Just as Facebook is starting to recover from last week's Congressional hearings with its CEO and releases statements on how it uses offsite user data, a new research report has emerged that may indicate another case of misused data.
This time, the culprit might be the "login with Facebook" API and the third-party JavaScript trackers embedded on websites that use it. First reported by Freedom to Tinker and TechCrunch, it seems that these trackers can be exploited to collect data like a user’s data including name, email address, age range, gender, locale, and profile photo -- to the extent of the information the user provided when it used this tool to log into the website.
As the name suggests, webmasters embed third-party JavaScript to, well, track user behavior on their sites -- things like how far someone scrolls down or where they clicked.
It can help digital marketers, for example, "figure out what works and what doesn't," says HubSpot Director of Web Development Dmitry Shamis, "and optimize your site as a result."
Tools like "login with Facebook" are designed to save new users time when creating a new account or enrolling in a website for the first time, by automatically populating fields (name, email address, et cetera) with information provided on their Facebook accounts, rather than requiring them to fill them in manually.
Many sites allow users to log in with Google in a similar capacity.
But now, it seems, vulnerabilities have been discovered in this system. In addition to granting the website or service in which the user is enrolling access to his or her data, third party javascript trackers embedded on that same site also receive access to the same data during the login process.
Here's an from Freedom to Tinker that visually explains how something like this works:
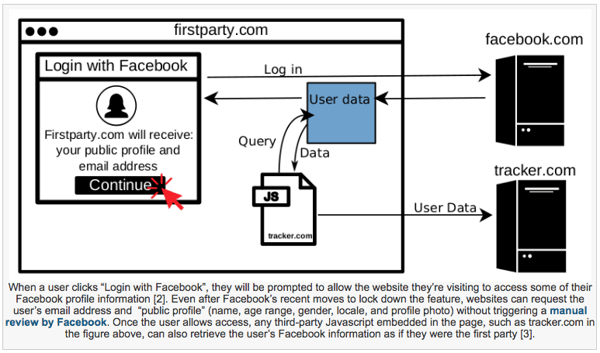
Source: Freedom to Tinker
What we haven't determined yet is how these trackers use the data once it's obtained. However, within the list of "offending" trackers discovered by Freedom to Tinker, it appears that the parent companies that manufacture them also offer "publisher monetization services based on collected user data," according to TechCrunch.
That could suggest a situation similar to the Cambridge Analytica one, in which an app developer collected personal data from users who opted into downloading it -- but then, improperly sold it to the data analytics firm.
But it doesn't stop there -- Freedom to Tinker discovered a second vulnerability. On some sites, after users log in with Facebook, it seems that some third-party trackers use that data to "deanonymize users for targeted advertising," which means that it can use login information to personally identify users, which is a privacy breach and typically not something that users agree to.
This happened with the site BandsInTown (possibly among others), which alerts people when the musicians they like are playing shows nearby. Logging in with Facebook helps BandsInTown track their favorite artists and let them know when they go on tour.
But as it turns out, there was yet another third-party tracker embedded in BandsInTown's iframe -- an HTML document that is embedded inside another, such document on a website -- which personally identified users logging in with Facebook, presumably for advertising purposes.
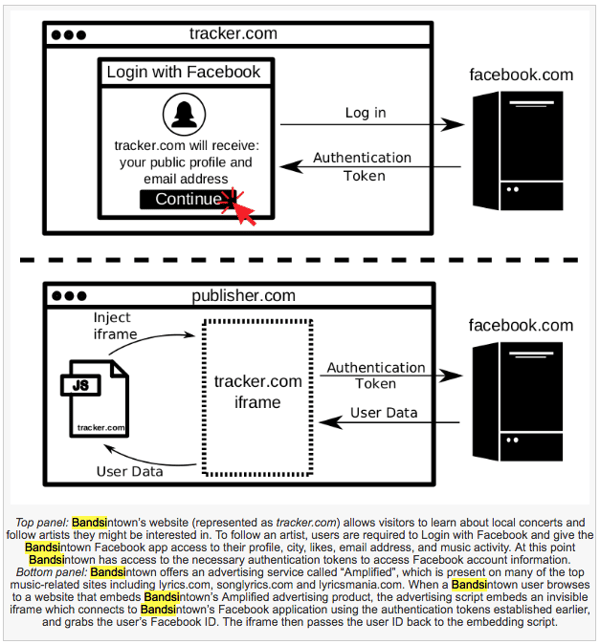
Source: Freedom to Tinker
After reaching out BandsInTown about the issue, Freedom to Tinker says it was told by the site that the flaw has been addressed and repaired.
And while Freedom to Tinker is sure to point out that these vulnerabilities are not the result of flaws within the login with Facebook tool -- and is rather due to what the site describes as a "lack of security boundaries between the first-party and third-party scripts" on the affected sites -- Facebook is certain to experience some blowback as a result of its user data once again being compromised.
When TechCrunch reached out to Facebook, it didn't receive a response being told that the social network was investigating the issue.
"This couldn’t come at a more inconvenient time for Facebook," says Henry Franco, HubSpot's social campaign strategy associate. "You can’t help but get the idea that a lifetime of shortcuts is finally catching up, putting the company on the defensive at a time when it needs all the wins it can get."
On top of that, Franco says, "I’m sure there will be more bad news as the company does a full audit of app developers on the heels of the Cambridge Analytica revelation."
HubSpot Product Lead Daria Marmer agrees that this report will only complicate things for Facebook -- as it not only has to make sure its own site is secure, but also needs to "police others on the web."
That might require playing catchup with sites that already have a method and operation for doing so, Marmer says. "Google does a good job of this: letting website owners know if their sites are insecure or getting attacked."
"As interconnected as today's systems are, it's easier than ever to create unintended side effects," says Ryan Stinson, HubSpot's manager of security engineering. "Events like these call for an even more heightened awareness of people's privacy needs, and taking a privacy-first approach to service."
This is an ongoing situation that continues to unfold as we await comment from Facebook and its aforementioned app audit is underway.
No comments:
Post a Comment